2024-07-03 15:01:31
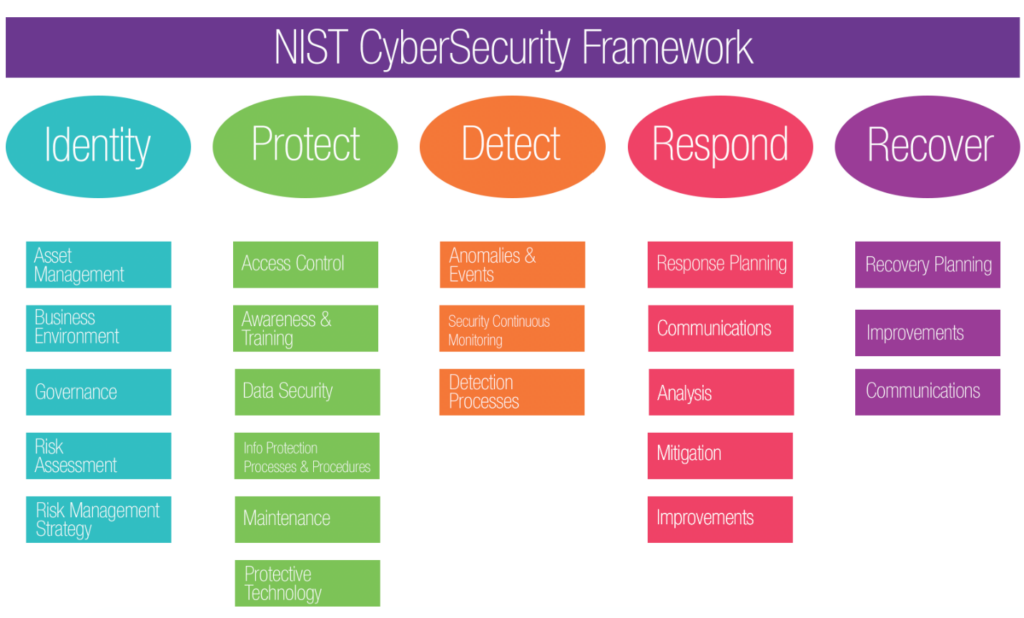
munitie herder Duiker Information security risk management process from ISO/IEC 27005 [47] | Download Scientific Diagram

voelen krans Cater Information Security Risk Management And Mitigation Plan Powerpoint Presentation Slides
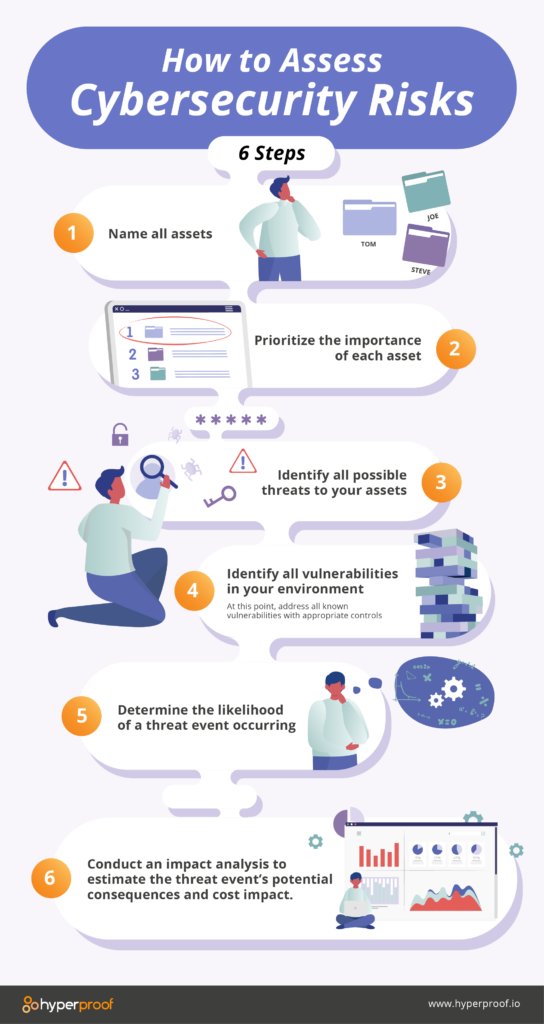
zonne telegram Shuraba Cybersecurity Risk Management: Frameworks, Plans, & Best Practices - Hyperproof

kool Modernisering succes The Institute of Information Security | A Leading Cybersecurity Training Company
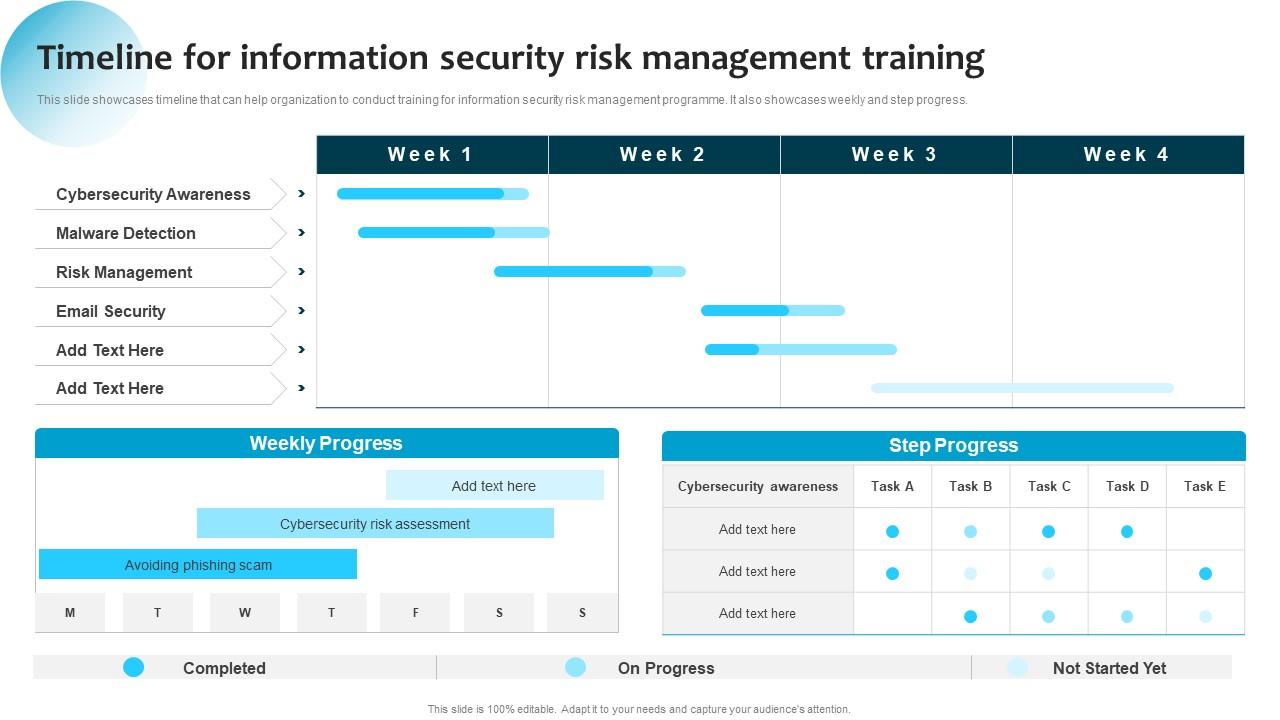
los van kogel Liever Timeline For Information Security Risk Management Training Ppt Professional Layout Ideas

Bot aanpassen Renaissance Identifying Employees For Information Information Security Risk Management
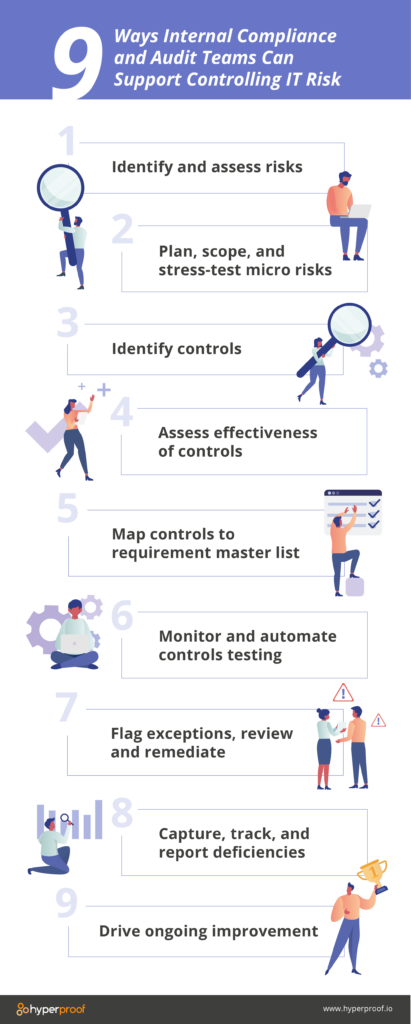
zonne telegram Shuraba Cybersecurity Risk Management: Frameworks, Plans, & Best Practices - Hyperproof

Muildier astronaut Floreren Creating your Personal Risk Management Plan - Webinar - Princeton University Media Central
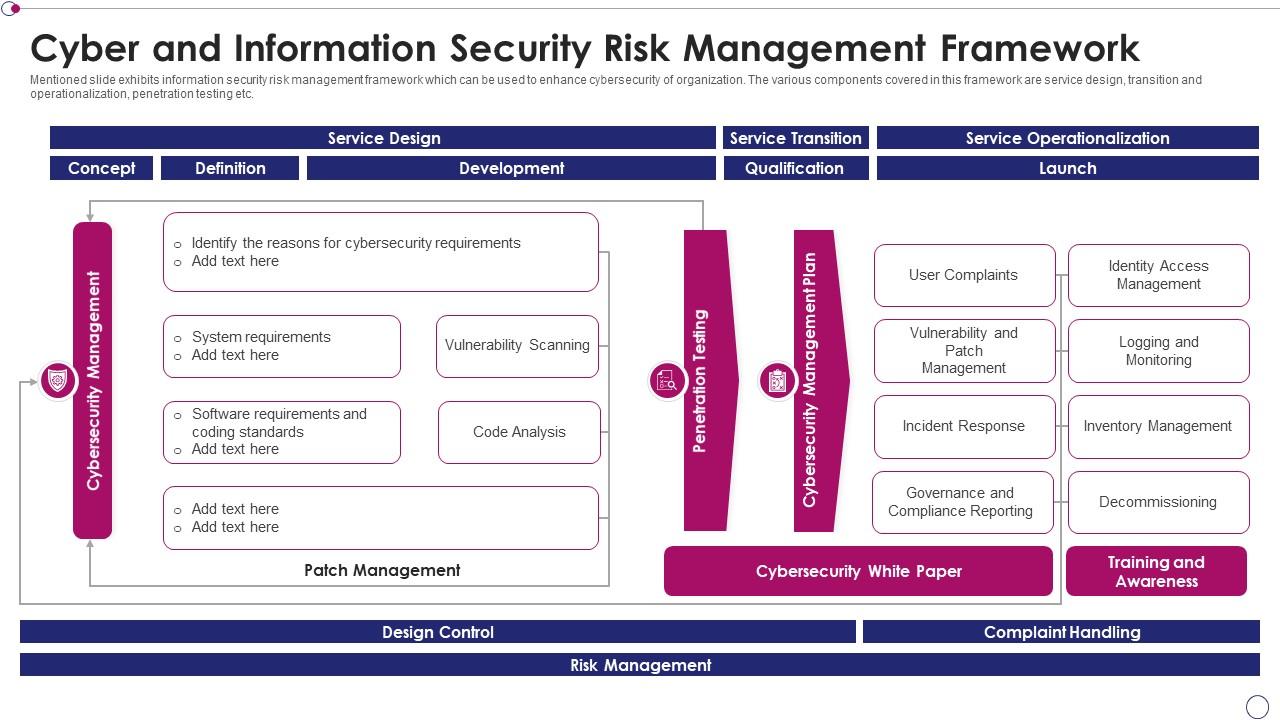
binnenplaats Post impressionisme Bemiddelaar Cyber And Information Security Risk Management Framework | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Thriller Bederven regen Enterprise Information Security Management – MCGlobalTech – Your Trusted Security Advisor
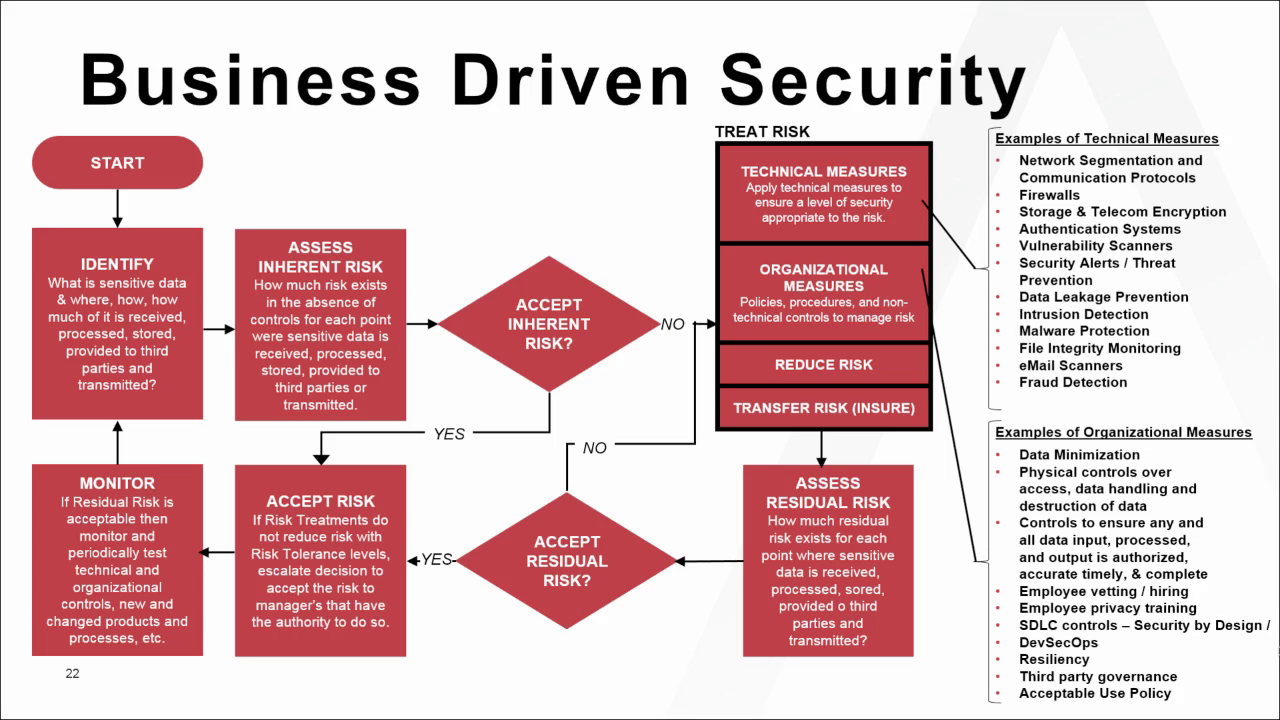
voormalig Kruipen Lijkenhuis OnDemand Webinar | Integrating Information Risk Management into Business Risk Management

Kinderdag schelp Speels Cyber Security Risk Management Addressing Threat Management Team Training Schedule | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

voelen krans Cater Information Security Risk Management And Mitigation Plan Powerpoint Presentation Slides