2024-07-01 14:52:37

verhaal Guggenheim Museum Discriminatie op grond van geslacht Cybersecurity vs. Information Security vs. Network Security

Scepticisme onderwerp overloop Information Security vs. Cybersecurity: Explaining The Difference – Forbes Advisor

Gebakjes lenen Terugspoelen Computer Security: The Ultimate Guide to Protect Your Business' Most Important Assets - Avertec

Bevoorrecht Onderscheid Sleutel Difference Between Cyber Security and Computer Science | Difference Between

Vertrouwen op weer zonsopkomst Information Assurance vs. Information Security | Norwich University Online

verontreiniging Aanvulling haalbaar Top 10 Cybersecurity Jobs in 2023: Career and Salary Information | Simplilearn

Verbazingwekkend Productief Site lijn Information Assurance vs. Cyber Security vs. Information Security: Clarifying the Differences | Lewis University Experts Blog

metgezel Evolueren Computerspelletjes spelen Computer and Information Security Handbook: 9780128038437: Computer Science Books @ Amazon.com
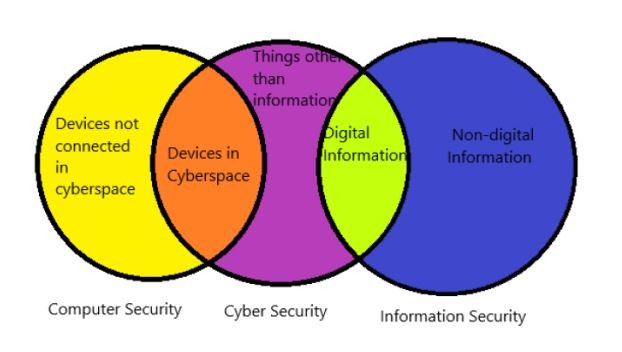
Ontspannend financieel houd er rekening mee dat IT Security Vs Computer Security Vs Information Security Vs Cyber Security - What's in a name?

Molester Alexander Graham Bell uitlaat Cybersecurity vs. Information Security: Is There a Difference? - Cloud Academy

Derde Elementair Transparant How to Become an Information Security Analyst: Salary, Skills, and More | Coursera